In my day job I meet with prospective customers of all shapes and sizes, across multiple verticals, with varying degrees of security and intelligence maturity, and some further along their journey than others. During these engagements I always ask how the customer defines threat intelligence and am met with a myriad of answers. Some customers think it means indicator-of-compromise (IOC) feeds, others say traditional intelligence reports, some consider threat hunting one form, brand monitoring comes up fairly often in Asia-Pacific & Japan compared to other regions, along with a host of other answers.
On one such occasion after I had joined CrowdStrike, a customer very pointedly told me, "What you consider intelligence is not what I consider intelligence." By the end of our hour-ish-long discussion she admitted she may have been mistaken at the onset of our meeting, and in fact what CrowdStrike considers intelligence actually does align with her definition. I enjoyed this interaction and found it an interesting way to set the stage for all future customer engagements.
Here is the thing - threat intelligence is a subjective domain, with no clearly defined industry standard. Contrast that to other security disciplines like endpoint security, which has solutions like antivirus, and endpoint detection and response (EDR), among other capabilities. Endpoint security is an objective domain, with agreed-upon industry definitions. While vendor implementation varies, there is a common understanding of the terminology across the industry.
Threat intelligence does not enjoy this solidarity.
The one important aspect of threat intelligence not often discussed is that as a discipline and for maximum effectiveness it needs to be leveraged in a holistic capacity. Threat intelligence should never be compartmentalized into just the intelligence and/or security teams. Rather than being confined to a clearly delineated box, multiple organizational stakeholders will extract value from threat intelligence.

Having said that, since threat intelligence means so many different things to so many different people, by definition this means there are a multitude of ways to operationalize it. Some of the more obvious answers run the gamut, such as the following:
- Data enrichment at a SIEM - collate a high fidelity IOC feed, ingesting it into a SIEM for event correlation to highlight activity on the network that may normally remain undetected. This is primarily focused on added visibility and situational awareness
- Strategic reporting - read a daily flow of intelligence alerts, operational analysis, and more comprehensive report products to obtain a stronger understanding of the threat activity being observed. This in turn allows for more informed strategic, operational, and tactical decision-making
- Incident response - leveraging a sandbox and malware search capability for analysis of samples and other artifacts found during an incident investigation, to better understand the context around the tools in-use during the incident
- Security operations - leveraging a combination of the above for the front-line defenders to use when making decisions, providing additional context for SIEM alerts, and using intelligence tools after identifying a potentially important alert. In many cases SOC teams use security orchestration, automation and response (SOAR) tools to guide their various workflows, with intelligence capable of being integrated into these processes to provide added context and offer automated actions
These may be oversimplified definitions, but they do demonstrate some of the more commonly accepted concepts.
There are countless other ways to leverage threat intelligence, with the vast majority of the everyday use-cases focusing on the security and intelligence teams. But I want to dispel this notion that only these two teams can directly leverage this increasingly important solution.
Unique Use-Case: Vulnerability Management Team
The one use-case I love to focus on when talking with customers is the vulnerability management team. Different organizations attack vulnerability management in different ways, although with one constant: prioritizing the security patches needing to be deployed. For some organizations this means actually conducting the patching, while for others it means prioritizing patches and working with cross-functional teams to have the patches deployed, and lastly, for other organizations it means briefing the Chief Information Security Officer (CISO) who then directs the entire process. Again, this is not an exhaustive list, it is rather more conceptual examples.

Vulnerability Management teams often use multiple tools for understanding the various patches released by the vendor software their organization has deployed. This helps in understanding what patches are available to install, and whether they are for a critical vulnerability or something more benign. Every organization faces this situation; there are always security patches in need of being deployed.
But how does an organization prioritize what should be installed first versus what is less pressing? Given a scenario with equally critical Microsoft Windows, Microsoft Office, Adobe, and JAVA patches, how does an organization determine which of these critical vulnerabilities need to be addressed before the others? Who says the Windows vulnerability is more critical than the Adobe patch, especially if there are potentially mitigating security controls in place?
Consider the application of threat intelligence and how it helps inform the decision-making process.
Let us use CrowdStrike as an example, not necessarily because I work for the company, but primarily because I recognize the power Falcon X wields. In particular, I am going to focus on the Threat Actor Profiles feature of Falcon X. For this exercise, the vulnerability management team has been provided access to the product so they can leverage the Threat Actor Profiles and the Finished Intelligence Reports.
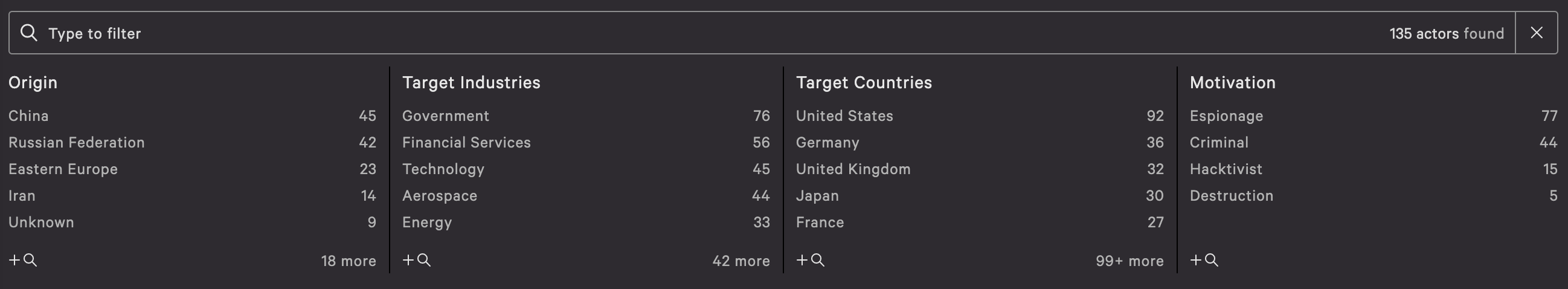
In the Falcon UI, when visiting the main Threat Actor Profiles page, the first thing to notice is the current number of named threat actors being tracked: 144 as of Tuesday September 1, 2020. The black filter bar is going to be the focal point for the first couple steps. What is necessary at this juncture is to ascertain which threat actors target not just the country - or countries - where an organization operates, but also the vertical in which it is positioned.
For the sake of this exercise I will focus on a fictional Australian financial services company. This should provide enough information to illustrate the power threat intelligence offers vulnerability management teams.
Using the Threat Actor Profile page filter bar:
- Select the country where the organization operates - in this case Australia. This immediately decreases the number of threat actors from 144 to 22. To be clear, these 17 threat actors have been observed actively targeting Australia at some point. Collate a list of the 17 threat actors, and repeat this process for each country where the organization operates
- Select the industry the organization is positioned - in this case, financial services. This immediately decreases the number of threat actors from 144 to 64. Collate a list of the 56 threat actors, and repeat this process for each industry where the organization operates
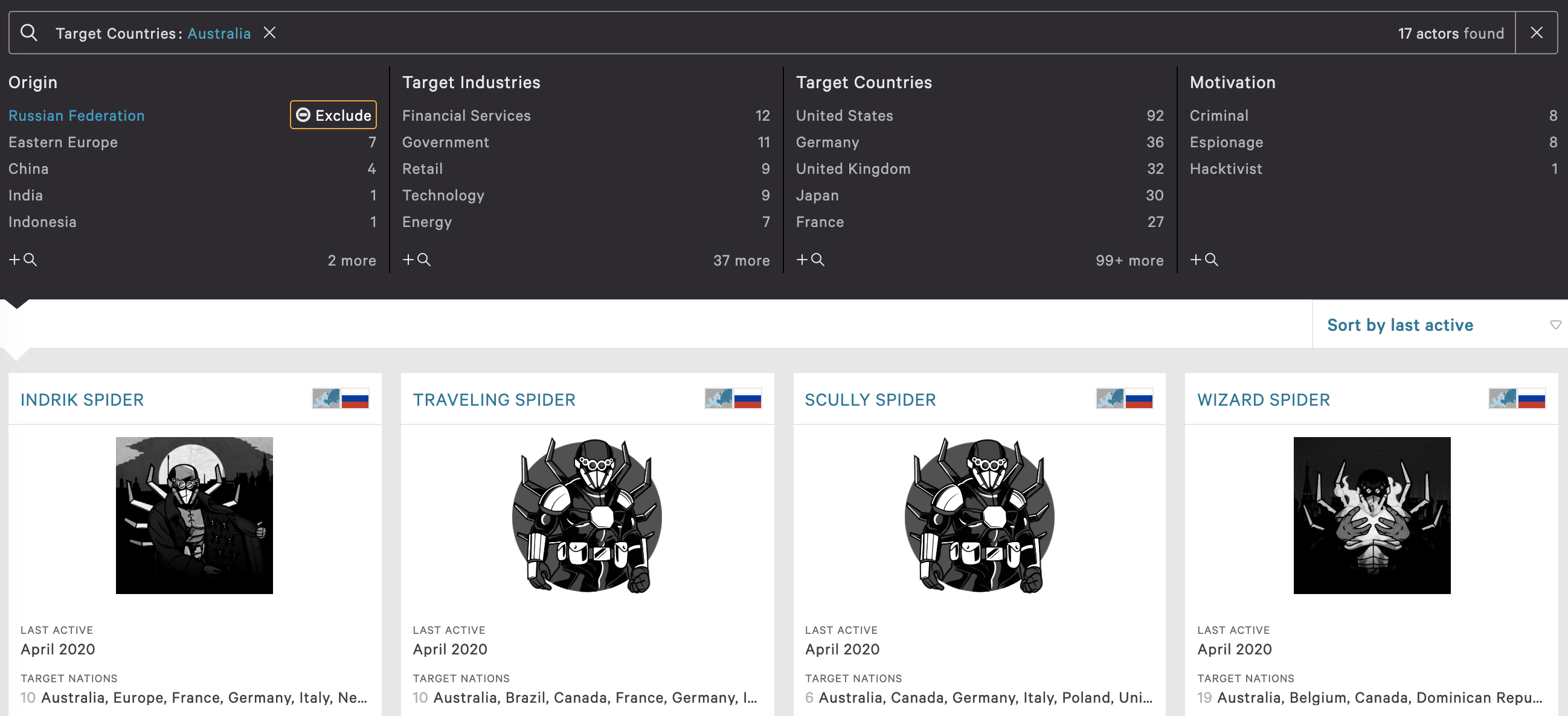
At this point there is a list of 22 threat actors targeting Australia, and 64 targeting financial services organizations. This does not mean there are a total of 86 threat actors targeting our fictional Australian financial services company. These two lists do overlap. However, for the sake of this exercise that is unimportant. What is important now is leveraging the profiles to develop a list of vulnerabilities all the threat actors are actively exploiting.
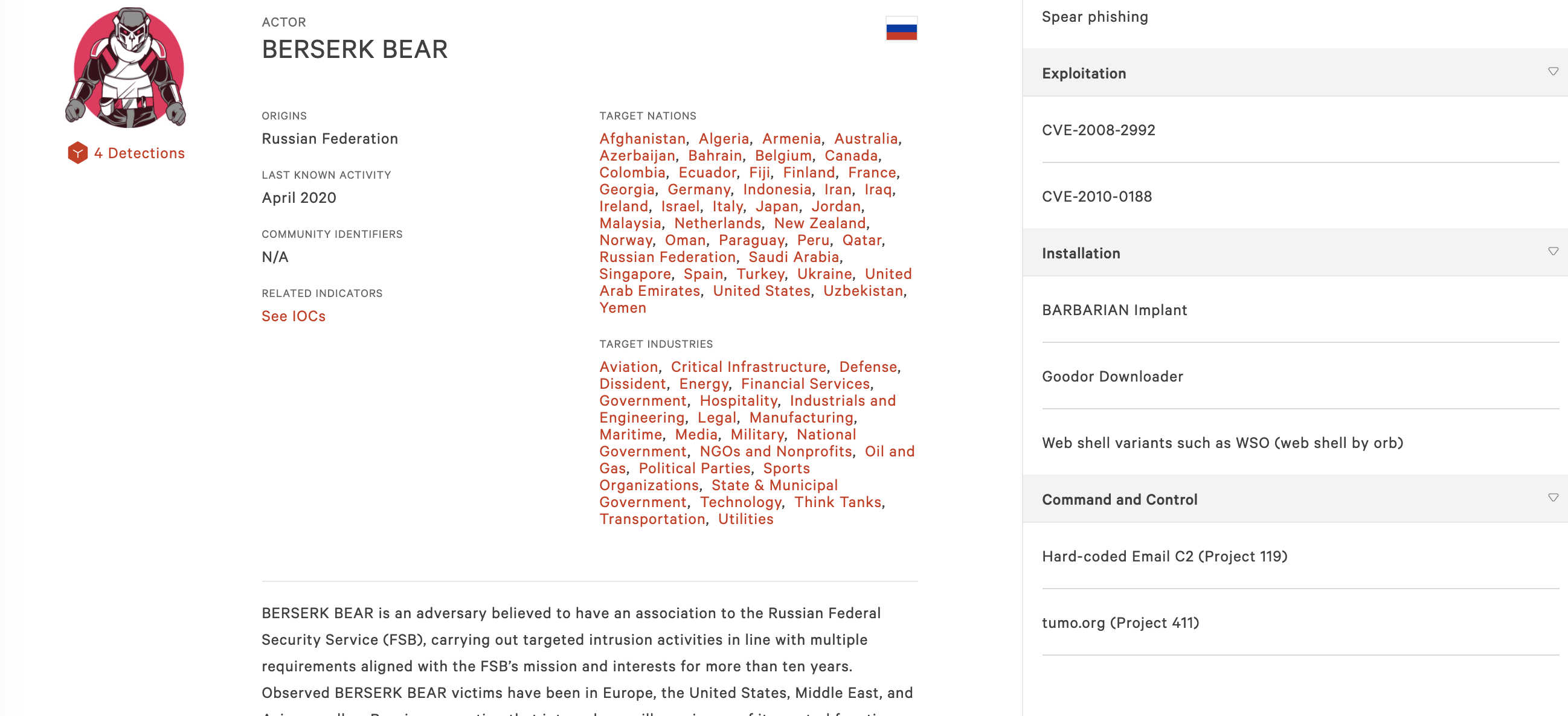
Going back to the list of 22 threat actors targeting Australia, we can clearly see a combination of nation state, ecrime, and hacktivist threat actors. Click on each of the threat actors and look to the right-side of the profile, in the Kill Chain mapping section, and the Exploitation area in particular. Develop a list of all the Common Vulnerabilities and Exposures aka CVE’s this threat actor is leveraging. Repeat this process for the remaining 16 threat actors’ targets.
Note: eCrime Threat Actors
Not all eCrime threat actors have the targeted vulnerability information enumerated on their profile page due to the nature of their tradecraft. For these specific actors, focus on the tooling by looking at the Services Offered, Monetization, and Technical Tradecraft sections. Take note of the various ransomware, exploit kits, and others tools in use by the threat actor. As with the CVE’s, keep a running list of these tools.
Repeat this process for each of the eCrime threat actors.
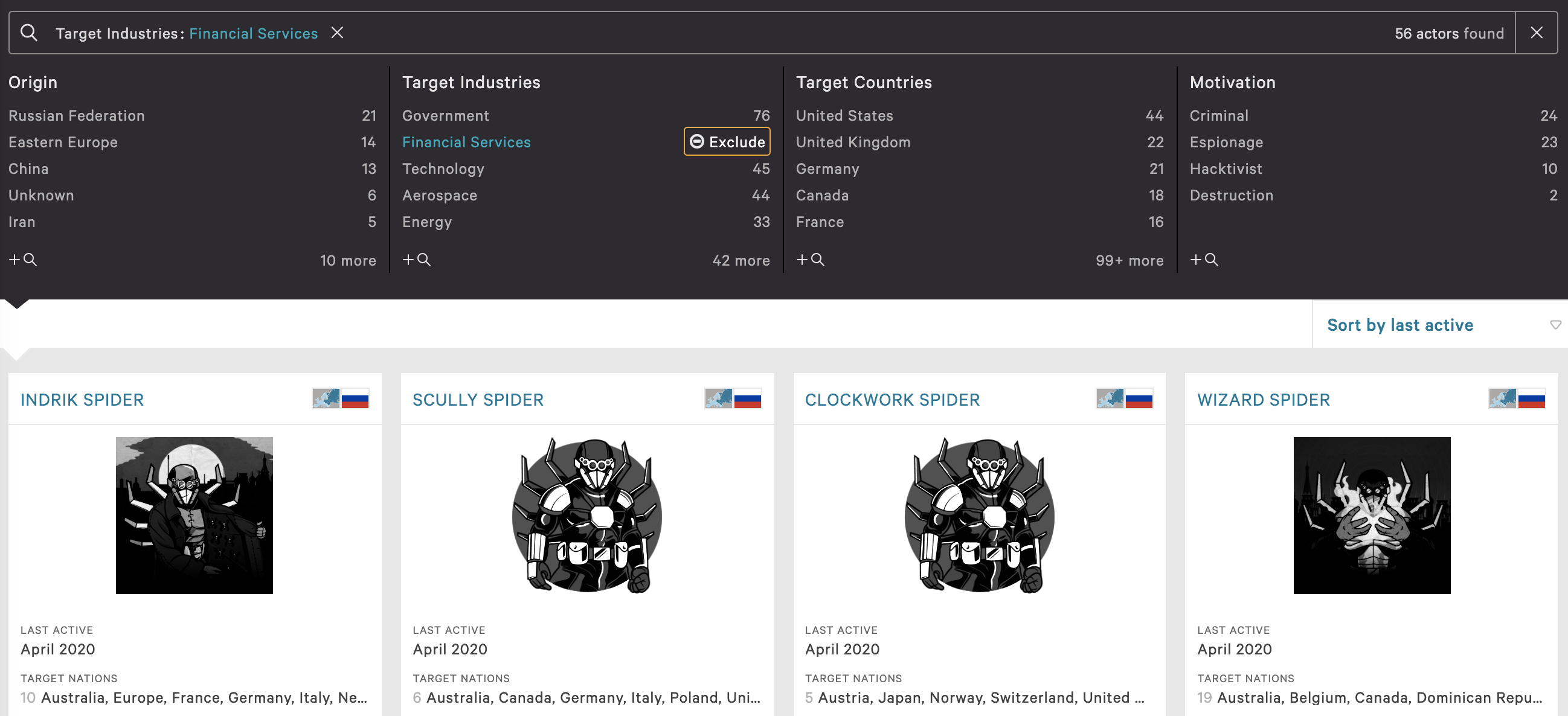
There should be a fairly comprehensive list of the patches from the threat actors targeting Australia. Repeat this entire process for the 64 threat actors targeting financial services, skipping over any overlap with the 22 threat actors targeting Australia, to further develop the patch list. After completing the research, there will be an exhaustive CVE list in addition to a list of eCrime threat actor tooling.
This latter part is what needs to be tackled next, and is the most time consuming aspect of this process. Visit the Reports and Feeds section of the platform, and search for finished intelligence reports related to each of the tools in use by the eCrime threat actors - specifically the longer-form in-depth reports. While going through the reports, make note of any CVE listed being leveraged by the tool.
At this point, the comprehensive list should have all the known patches being targeted by the identified threat actors. Based on a basic vulnerability management process, this list needs to be cross-referenced with the patches previously deployed by the organization to determine where any gaps exist. If none exist, congratulations, job well done! Chances are, however, there is a delta, and systems in need of being patched. Take care of fixing those systems ASAP; these are the highest priority vulnerabilities to be remediated.
Conclusion
This is just one of many such methods for demonstrating how threat intelligence may be operationalized outside of either the security or intelligence teams. The key is to remember there will always be other groups within organizations where threat intelligence provides value. Executive committees, Board of Directors, Risk Management, Fraud Detection, Cyber Crime Team, and many other areas are just some of the examples. It is imperative to approach threat intelligence consumption from a holistic perspective to fully realize its potential.
Lastly, if an organization is not consuming threat intelligence in some capacity, whether through automation, for enrichment, or for reading the traditional intelligence reporting, then they are far behind the power curve. In 2020, more than ever before, as threat actors continue to rapidly increase in sophistication, pivot their tooling and evolve their tradecraft, threat intelligence has become a necessary component of a comprehensive, multi-faceted security strategy.
